Binary Vulnerability Analysis
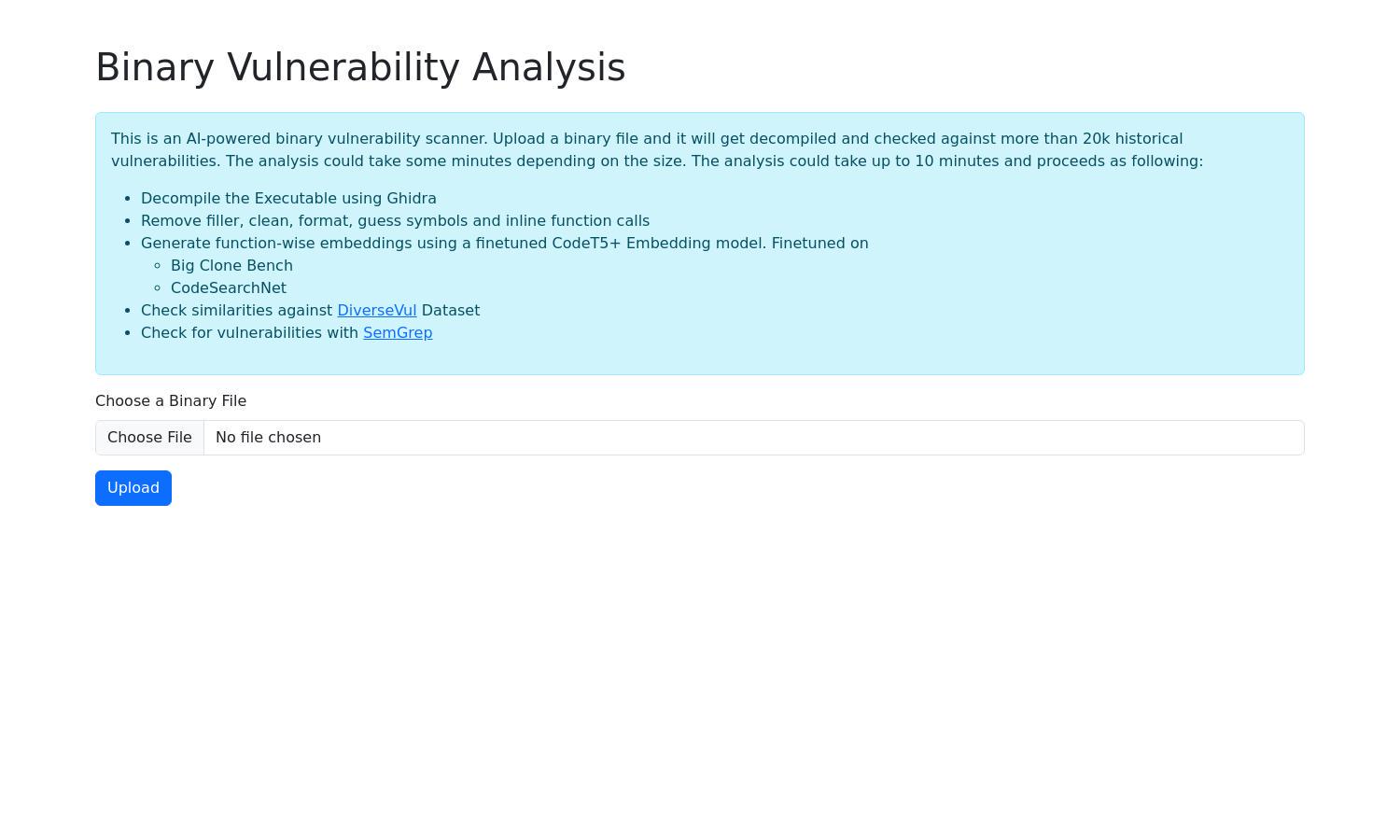
About Binary Vulnerability Analysis
Binary Vulnerability Analysis offers an advanced AI-driven solution for detecting vulnerabilities in executable files. Perfect for developers and security professionals, it streamlines the process of identifying risks by using sophisticated decompilation and analysis tools. The unique embedding model enhances detection accuracy and efficiency.
Binary Vulnerability Analysis provides various pricing tiers to facilitate different user needs. The basic plan allows for essential scanning, while premium subscriptions offer advanced features and priority support. Upgrading to higher tiers unlocks additional analysis capabilities, ensuring comprehensive security for all executable uploads.
The user interface of Binary Vulnerability Analysis is designed for intuitive navigation, providing users with a streamlined experience through its clean layout and easy-to-use features. Each step is clearly defined, helping users to efficiently upload files, track analysis progress, and view results seamlessly.
How Binary Vulnerability Analysis works
To use Binary Vulnerability Analysis, users begin by uploading their binary files through the platform's web interface. The process initiates decompilation using Ghidra, followed by cleaning and formatting the code. Then, the system generates function-wise embeddings with a specialized model before comparing against known vulnerabilities, delivering precise insights efficiently.
Key Features for Binary Vulnerability Analysis
AI-driven Binary Analysis
The AI-driven binary analysis feature of Binary Vulnerability Analysis utilizes advanced machine learning algorithms to detect vulnerabilities in uploaded files. This unique capability ensures accurate identification of potential security threats, providing users with crucial information to fortify their applications against evolving risks.
Comprehensive Vulnerability Database
Binary Vulnerability Analysis boasts access to a vast vulnerability database, allowing users to check their binaries against over 20k historical threats. This extensive coverage empowers developers to enhance their software security, ensuring timely identification and remediation of potential vulnerabilities within their applications.
Enhanced Code Decompilation
The enhanced code decompilation feature of Binary Vulnerability Analysis uses Ghidra to transform executable files into readable code. This unique capability allows for deeper analysis and understanding of potential vulnerabilities, ensuring users receive comprehensive insights into the security posture of their applications.
You may also like: